This is the sequel to an earlier post by Smut Clyde and Tiger BB8, who now have unmasked the mastermind behind the grand scam of plagiarism, peer review fraud and self-citations for which Springer seems to be somewhat ashamed while Elsevier sees a business opportunity. The affair is even more mental that it initially seemed.
The fraud kingpin, the spider of that criminal web, the Godfather of the pseudoscience syndicate who created garbled nonsense “papers” which he either plagiarised from online sources or stolen as reviewer, has been a certain young Chinese IT nerd named Luming Zhang, all along. Best bit: Zhang is not even coauthor on those counterfeit surveillance technology garbage he stuffed into the Springer journal Multimedia Tools and Applications (where they were now retracted, only to re-appear at Elsevier). Zhang namely created throw-away email addresses to invent or to steal identities of corresponding authors of papers he himself was not listed on, for all we know maybe even with their approval, and maybe even in return for a bribe or favours of some kind. The goal of this elaborate scam: to boost Zhang’s own citations in the field of internet surveillance, which apparently not only advanced his academic career in that one-party state founded on mass oppression, but also earned him a collaboration with the Chinese military. On the plus side, if this is the kind of experts and the technology the Communist Party of China intends to deploy to control its own citizens, there is still good hope for democracy and freedom of thought to grow in the shadows. Go Luming Zhang, and go Springer and Elsevier!

“Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations”
By Smut Clyde and Tiger BB8
That is how Tengfei Wu can extend the borders of Chinese jurisdiction to annex Singapore.

 Meanwhile, revelations continue in the ripping yarn of papermills, peer-review shenanigans and peer-reviewer manuscript piracy in the august pages of Multimedia Tools & Applications (MTAP). It is enough to undermine one’s faith in the promises of automated, pervasive, panopticon-state surveillance through cyberspace and meatspace which populate the pages of that journal. It all came as a surprise, for the title led me to expect a focus on hard-to-pigeonhole digital artforms.
Meanwhile, revelations continue in the ripping yarn of papermills, peer-review shenanigans and peer-reviewer manuscript piracy in the august pages of Multimedia Tools & Applications (MTAP). It is enough to undermine one’s faith in the promises of automated, pervasive, panopticon-state surveillance through cyberspace and meatspace which populate the pages of that journal. It all came as a surprise, for the title led me to expect a focus on hard-to-pigeonhole digital artforms.
The story so far is that someone was confiscating manuscripts which had been submitted to MTAP, then publishing them in the names of cronies and customers, somehow bypassing actual peer-review in the process. We provisionally pointed the finger at Yiyang Yao, nominally author of many of the pirated MTAP papers (and their digital doppelgangers at JVCIR, the Journal of Visual Communication & Image Representation); and / or Caiyou Zhang, his colleague at the State Grid Zhejiang Electric Power Company. What we had earlier missed, though, was the “Citation Plantation” phenomenon.
By way of (roundabout) explanation, here is Yiyang Yao’s email address on a paper where he was Corresponding Author. It appears to be a one-time throwaway identity, a ‘nonce‘ as the linguists and Infosec people say:
* Yiyang Yao
junli1778@126.com
A pattern begins to emerge when we look at the e-addresses provided for other fake papers. They’re all bogus, to keep the putative authors out of the loop, and coined by the same person… Some person who really likes the number 1778. If you ever find that dude’s credit card, you know what PIN to try.
zhengyongjun1778@126.com
zhangcaiyou1778@126.com
junli1778@126.com
junli1778@gmail.com
jiangzhengwei1778@126.com
guiliye1778@126.com
lilin1778@126.com
xiongchao1778@126.com
 Let’s look at the use of “junli1778@gmail.com“. The context is the retracted 2017 paper “Wireless security and control technique in boardcast [sic] television signal transmission“, by Tengfei Wu again – now affiliated to “China Anhui Broadcasting Corporation, Hefei” and no longer (if ever) at Singapore National University of China. It relates the lessons about security and interruption-proofing he learned from keeping the Anhui television network on-air, and it earned him an award. The language is far from standard English, hinting at several cycles of Google Translate but not always entirely comprehensible. But we should cut some slack for an author whose first language is perhaps Gujarati or Hindu, judging from Figure 3 (“An introduction of the total monitoring center platform includes eight sub-program modules”), which was evidently drawn up to illustrate someone’s experiences at ensuring uninterrupted television boardcasts broadcasts from Ahmedabad.
Let’s look at the use of “junli1778@gmail.com“. The context is the retracted 2017 paper “Wireless security and control technique in boardcast [sic] television signal transmission“, by Tengfei Wu again – now affiliated to “China Anhui Broadcasting Corporation, Hefei” and no longer (if ever) at Singapore National University of China. It relates the lessons about security and interruption-proofing he learned from keeping the Anhui television network on-air, and it earned him an award. The language is far from standard English, hinting at several cycles of Google Translate but not always entirely comprehensible. But we should cut some slack for an author whose first language is perhaps Gujarati or Hindu, judging from Figure 3 (“An introduction of the total monitoring center platform includes eight sub-program modules”), which was evidently drawn up to illustrate someone’s experiences at ensuring uninterrupted television boardcasts broadcasts from Ahmedabad.
I am not convinced that Figure 2 (“An introduction of the eal-time monitoring stations transmit various operating states”) is an adequate depiction of the challenges and technology of contemporary broadcast media.
As for Figure 1 (“An overview of our proposed security system”), it has appeared before: for instance in an InTechOpen book from 2010, by Mahmudov & Fedosov, where it was captioned “Global model of digital broadcasting system”.
What concerns us most, though, is the disproportionate amount of the References section given over to the works of Luming Zhang (henceforward just LZ).

LZ was originally at Zhejiang University (ZHU) and graduated in 2012, studied in Singapore with Zimmermann as a 2013-2014 post-doc, and progressed to the School of Computer Science at Hefei University of Technology where he is still listed on the faculty, but is now back at ZHU as a researcher.

Commenter ‘Me’ observed that clusters of citations for LZ’s work irrupt into a remarkable number of MTAP papers, as if this were part of the journal’s manuscript-formatting conventions. In total he has received over a thousand references from MTAP, which is valuable currency in the academic-promotion economy. It is as if LZ had somehow suborned the journal’s peer-review system, so that the citation advertisements for his career are sometimes the payloads of fake papers (arranged along a spectrum, from confiscated manuscripts that were sold to other authors, to meaningless collages of copy-pasted gibberish) and sometimes enforced on legitimate authors as the price for publication there. The parsimonious explanation, then (h/t to ‘Me’!) is that LZ is the contributor of those self-citation delivery vehicles… calling him ‘author’ is too strong a term. A German observer reached the same conclusions.
 LZ does indeed turn out to belong to MTAP’s honorable hard-working peer-reviewing corps. He was an editor of the Special Issue of MTAP (“Multi-source Weak Data Management using Big Data”) where the malfeasance was too pervasive and came to light. He also works closely with Tengfei Wu… jointly they own a software company in Hefei. They are two buttocks of one bum [T. Sturge Moore 1911]. While one of those paper-shaped MTAP hairballs which with we began, nominally written by Tengfei Wu during his sojourn in Singapore (China), in fact carries LZ’s e-address for correspondence. No ‘1778’ disposable identity!
LZ does indeed turn out to belong to MTAP’s honorable hard-working peer-reviewing corps. He was an editor of the Special Issue of MTAP (“Multi-source Weak Data Management using Big Data”) where the malfeasance was too pervasive and came to light. He also works closely with Tengfei Wu… jointly they own a software company in Hefei. They are two buttocks of one bum [T. Sturge Moore 1911]. While one of those paper-shaped MTAP hairballs which with we began, nominally written by Tengfei Wu during his sojourn in Singapore (China), in fact carries LZ’s e-address for correspondence. No ‘1778’ disposable identity!
It seems that LZ is happy with the ‘zglumg’ abreviation as he has been using it since his PhD study at ZHU, later when doing a post-doc in National University of Singapore (zglumg@nus.edu.sg), and currently as a researcher in ZJU again.

It isn’t really necessary to look at another of these MTAP confections, but they are amusing.
Until its retraction, “Utilizing a deep learning model to enhance video credibility verification system” bore the names of Yongjun Zheng (zhengyongjun1778@126.com), Yinjie Wei, Wenjun Li and Yi Lu. The title sounds meaningful enough, apart from the empty adjective “Deep” which needs to be read in the voice of a stoned hippie… but the authors wandered unchecked through a garden of bright images, so sentence fragments about ‘video credibility verification’ alternate with fragments about hacker attacks on industrial software (and how to thwart them). My guess is that someone submitted a paper focused on the Industrial Software Security angle, which collided in the office printer with a few other documents so they all got mashed together and nonsensical (also unrecognisable to the real authors, but only as a side-effect).
Figures are pilfered from various sources. Figure 2 (“The flowchart of our deep industrial analysis process”) can be traced to a 2012 discussion of the STUXNET worm attack.
The legend for Figure 3 is somewhat opaque: “In the structure of our CNN starting module, module (a) and (b) are proposed in [22] image classification, the execution module and memory module and calculate the budget even in the strict constraints (b) is an expanded (a) to promote the coarse grid”.
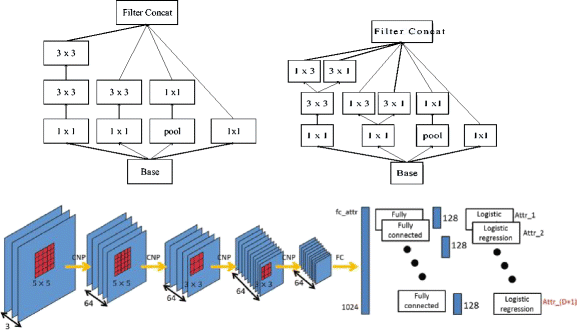
The lower part of Fig 3 had earlier appeared in an unpublished but arXived manuscript by LZ, “Describing Human Aesthetic Perception by Deeply-learned Attributes from Flickr” (drawing from the same post-doc project as his 2016 paper with Richang Hong & Dacheng Tao). He really likes the word “deep” in its many forms, believing it to have talismanic virtue.

The upper part is the “Inception Module convolution” architecture for computer vision, courtesy of Szegedy and colleagues working at Google. It took its present form when 2016 Qi et al. replotted it in “Deep feature representation and multiple metric ensembles for person re-identification in security surveillance system” – crediting Szegedy et al., so that’s all good. But then it found its way into “Utilizing a deep learning model…”…
AND as Figure 1 of “A method of multi-criteria set recognition based on deep feature representation” by “zhangcaiyou1778@126.com” et al….
AND as Figure 5 of “Efficient object analysis by leveraging deeply-trained object proposals prediction model” by Bo Dai, “Yiyang Yao” / junli1778@126.com et al….
AND as a digital doppelganger of “Efficient object analysis…” at JVCIR (no contact details provided).

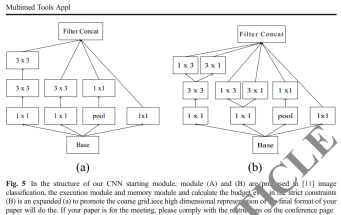
I need to say that I am not making up, but only highlighting the shared legend:
Fig. 1 / 5 In the structure of our CNN starting module, module (A) and (B) are proposed in [22] image classification, the execution module and memory module and calculate the budget even in the strict constraints (B) is an expanded (a) to promote the coarse grid.ieee high dimensional representation of the final format of your paper will do the. If your paper is for the meeting, please comply with the restrictions on the conference page
Both those latter papers were retracted for the usual reasons – “authorship manipulation and an attempt to subvert the peer review process” – but also because of the extent of plagiarism from Qi et al. (2016). The picture went once too often to the well and is broken at last. Alas, plagiarism is not an issue for the editors of JVCIR.
Apart from this industrial-scale plundering of text and illustrations, Qi et al. (2016) contains a familiar Citation Plantation for LZ’s benefit… presumably inserted as the toll for acceptance in MTAP. In fact the same citation block turns up in a 2017 paper by the same team. Meibin Qi and co-authors are in the Computer and Information faculty at Hefei University of Technology – which is to say LZ’s colleagues at the time – but that did not save them from his depredations.

The lesson here is that an undigested bolus of LZ citations is neither sufficient evidence nor necessary evidence to establish the bogosity of a paper. It may be enough to require a correction to the paper.
I cannot resist two last excerpts from “Efficient Object Analysis…” They show what can happen when adversarial Google translations and Roget substitutions, intended to defeat plagiarism detectors, go horribly wrong.
“Traditional intravenous infusion is an effective method in complex scenes such as target occlusion, sudden change, illumination, interference and so on.
The structure of this paper is as follows. Securities and Exchange Commission, sec. 2. We introduce the estimation of object importance. Securities and Futures Commission, sec. Three. We studied background estimation. Securities and Exchange Commission, sec. 4 fusion detection is given. Securities and Exchange Commission, sec. 5. We sent the experimental results and evaluation results in advance. Finally, we conclude that this is effective in SEC. Six.”
While from “Deep feature representation”, the process of plagiarism-hiding engarblement turned the “KISSME algorithm” in the original text into a cybernetic insult.

Our informant notes that LZ is not the only MTAP peer-reviewer whose papers have been so influential, recognised by over a thousand MTAP citations… many inserted en bloc at the re-submission stage, often with no obvious relevance to the text. The problem may be more widespread, and editors might also want to look at the reviewing activities of Ye Liu. But this post is already long enough without going down that rabbit-hole.
 Anyway, the steady stream of MTAP Retractions suggests that the editors have accepted that they have a problem and are trying to cleanse their Augean stable. It all raises the purely hypothetical question: At what point should a board of Editors accept that their journal has been systematically corrupted and pimped out by its peer-reviewers, and announce that nothing they have published for the last few years deserves any credence at all?
Anyway, the steady stream of MTAP Retractions suggests that the editors have accepted that they have a problem and are trying to cleanse their Augean stable. It all raises the purely hypothetical question: At what point should a board of Editors accept that their journal has been systematically corrupted and pimped out by its peer-reviewers, and announce that nothing they have published for the last few years deserves any credence at all?
Now if I were to pick a dozen or so publications from my CV, abusing peer-reviewer powers to coerce other researchers to promote them and up-vote my reputation, I would focus on papers with special relevance to my employment or research-grant ambitions. I would leave out the ones about trebuchets and the Renaissance tradition of Memory Palaces.
And we saw earlier how many of these bogus MTAP papers could interest governments (purely hypothetical ones) that would like to monitor the movements, actions, and on-line activity of every citizen, through ubiquitous automated video-camera and social-media surveillance (a timely subject right now). It is impossible to delve into this literature without hearing soft-rock stalker anthems by The Police playing in the back of one’s mind. Anyway, this focus is especially acute in LZ’s Citation Plantations… they come across as a job application.
One can only speculate how much this strategy of reference extortion contributed to LZ’s ascent from Hefei University of Technology (a regional institution) to Zhejiang University (among the top five in China). His position there is sensitive, and rumoured to have military sponsorship, so we are reluctant to ask too many questions. His office is unlisted.
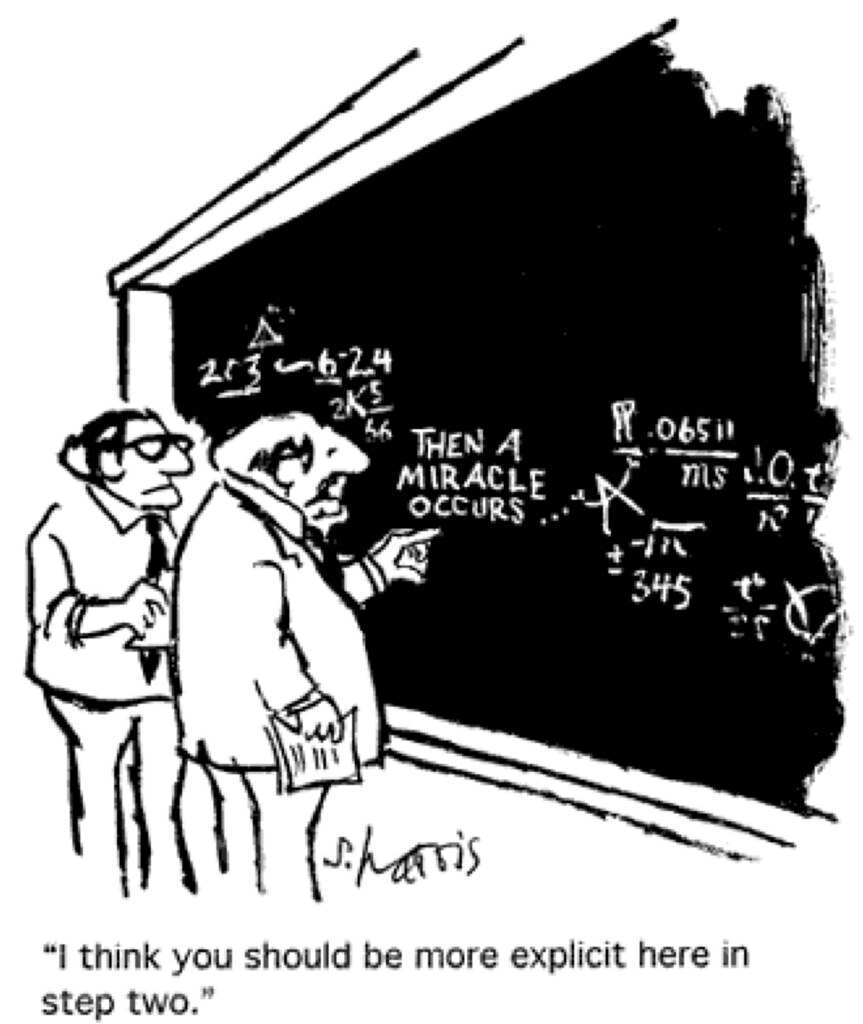
I am not entirely convinced that LZ is the right person to enhance a dystopian government’s mass-surveillance capability. His publications are too reliant on talismanic phrases like “Deep” and “Big Data” and “Lightly supervised machine learning” in lieu of details; and on diagrams of the relationships of black-box modules; and on plagiarism. His models need to be more explicit in Step Two. And the predictable ‘1778’ pattern for his one-time identities is terrible trade-craft. From the perspective of an outside observer, of course, he is the perfect researcher for a dystopian government to waste money on, rather than giving it to a non-charlatan who might achieve results.
If it turns out that LZ had no direct hand in the production of all these papers, and that they all emerged from a neural network he designed and trained, then he will have earned every yuan.

Donate!
If you are interested to support my work, you can leave here a small tip of $5. Or several of small tips, just increase the amount as you like (2x=€10; 5x=€25). Your generous patronage of my journalism will be most appreciated!
€5.00



Amazing. Identity changes I have seen for some authors coming from another Asian country, Pakistan.
LikeLike
“kiss my algorithm”.
Brilliant screw-up. Thanks for sharing!
LikeLike
Now also on IEEE:
Sun, X., Zhang, L., Wang, Z., Chang, J., Yao, Y., Li, P., & Zimmermann, R. (2018). Scene categorization using deeply learned gaze shifting Kernel. IEEE transactions on cybernetics, 49(6), 2156-2167.
https://ieeexplore.ieee.org/document/8358008
LikeLike
As of today, Luming Zhang is not listed on College of Computer Science (CCS) of Zhejiang University (ZJU). Previously, Zhang was listed as the vice chair person of CCS’ Artificial Intelligence department but does not appear on AI department list of faculty. So, it looks like ZJU has most likely secretly removed Zhang without any announcement of an investigation had ever been conducted.
Leonid, I cannot post screenshots to backup my statement here on your website.
LikeLike
At last there is some progress to report! Unexpectedly, the editors of J, of Vis. Communications & Image Representation have retracted 10 LZ-related papers for duplication. The retraction notices are variations on a theme, all condemning the duplicity of the authors and none hint that lax or negotiable behaviour by special-issue guest editors contributed to the acceptance of the papers.
Three of these Notices are dated 16 March 2020. One is 12 July 2019. In the other cases, the Notices replace the original entry in the journal’s website, rather than being separate and separately-dated documents, so they can’t be dated precisely.
http://retractiondatabase.org/(X(1)S(lcdtdzrskfjlbu11r4lkl5ly))/RetractionSearch.aspx?AspxAutoDetectCookieSupport=1#?AspxAutoDetectCookieSupport%3d1%26jou%3dJournal%2bof%2bVisual%2bCommunication%2band%2bImage%2bRepresentation
LikeLike
Not to be out-done, over at MTAP the number of recent retractions.has swelled to 34. 5 new ones dated April 1 2020, on top of 16 from June 2019, and 13 from May 2019. There may be more that are not yet visible… I get the impression that these retraction notices are not appearing until the corresponding paper has officially reached the status of ‘Published’, so while they are at the level of ‘Early View’ (accepted but not paginated in a specific issue), they may be retracted as well without any notification to this effect.
I hasten to add that not all these papers bear the hallmarks of LZ involvement (that is, the References sections are not always citation plantations. Not all of them had been flagged here or in Pubpeer threads, so kudos to the MTAP editors for belatedly scanning for plagiarism / duplication. For instance, “A novel semantic smoothing method based on log-bilinear model for bayesian text classification” (https://pubpeer.com/publications/C3373C5B7711670082710508C0AFCE) was plagiarised from a 200 Conference Proceedings report.
LikeLike
But then there are papers like “Detecting anomalous emotion through big data from social networks based on a deep learning method” (https://pubpeer.com/publications/8E265D43871BA6728E7122615441AE) which was self-plagiarised from an earlier paper with two of the same authors. Those authors are at Hefei University, a clue that LZ was involved. Another clue is the five papers inserted clumsily into the References:
Luming Z, Mingli S, Zicheng L, Xiao L, Jiajun B, Chun C (2013) Newblock probabilistic graphlet cut: Exploring spatial structure cue for weakly supervised image segmentation. In: Proceedings of CVPR2013
Luming Z, Yahong H, Yi Y, Mingli S, Shuicheng Y, Qi T (2013) Discovering discriminative graphlets for aerial image categories recognition. IEEE T-IP 22(12):5071–5084
Luming Z, Yi Y, Yue G, Changbo W, Yi Y, Xuelong L (2014) A probabilistic associative model for segmenting weakly-supervised images. IEEE T-IP 23(9):4150–4159
Luming Z, Yue G, Roger Z, Qi T, Xuelong L (2014) Fusion of multi-channel local and global structural cues for photo aesthetics evaluation. IEEE T-IP 23(3):1419–1429. ISSN:1057-7149
Luming Z, Yue G, Rongrong J, Qionghai D, Xuelong L (2014) Actively learning human gaze shifting paths for semantics-aware photo cropping. IEEE T-IP 23(5):2235–2245. ISSN:1057-7149
I am personally concerned by the explanation given for why the authors’ research was important: “facilitating the government in monitoring public opinion and public safety through social network, prevent the spread of irrational emotions over social network or even in the real world, and respond timely to the possible negative incidents to prevent criminals attempting to spread rumors [38] through microblogs [9]”
In other words, they provide an authoritarian government with a useful tool for automatically recognising dissident views and facts, and removing them from social media.
LikeLike
Another exercise in self-plagiarism: “Image retargeting based on self-learning 3D saliency
for content-aware data analysis” (https://pubpeer.com/publications/60C0EAA0116247BF723A34A36D9A33), which is a repackaged version of a 2015 paper in “Signal Processing”, Yanxiang Chen being the first author of the 2015 version and the last author of this 2017/2020 version. Chen’s presence at the Hefei University of Technology is the only hint that LZ was editorially involved in the acceptance of this version.
LikeLike
Here’s a case of manuscript piracy where the unpublished paper was sexed-up with LZ citations: “Internet-scale secret sharing algorithm with multimedia applications” (https://pubpeer.com/publications/B0F8031B1A578EBC48ECC9EF18D64F).
https://pubpeer.com/storage/image-1588035576698.png
There’s no connection between Refs 13 to 30 and the links to them in the text. It’s as if the process of piracy included replacing those References in the original manuscript with LZ’s entire CV.
“A new deep representation for large-scale scene classification” (https://pubpeer.com/publications/9C0D43084B3F785AE640375971CC78) was plagiarised from a chapter in “Lecture Notes in Computer Science (2011)”; sexed up with LZ’s CV again; published in MTAP; then republished in JVCIR.
https://pubpeer.com/storage/image-1588034415273.png
LikeLike
Pingback: The Men Who Stare at Ketotic Cows – For Better Science